Are you looking for a secure and efficient way to manage your IoT devices remotely? AWS IoT SSH Tunnel might be the solution you need. As the Internet of Things (IoT) continues to grow, managing and securing remote connections to your devices becomes increasingly important. AWS IoT SSH Tunnel provides a secure method for establishing remote connections, ensuring your data remains protected while allowing seamless device management.
In today's digital landscape, where security breaches are becoming more sophisticated, having a reliable remote access solution is crucial. AWS IoT SSH Tunnel offers a robust framework that combines the power of AWS IoT services with secure shell (SSH) technology. This combination allows you to maintain secure connections to your IoT devices while leveraging the scalability and reliability of AWS infrastructure.
This comprehensive guide will walk you through everything you need to know about AWS IoT SSH Tunnel. From understanding its core components to implementing it in your infrastructure, we'll cover all aspects of this powerful tool. Whether you're an IoT developer, system administrator, or IT professional, this article will provide valuable insights and practical information to help you make informed decisions about your remote access strategy.
Read also:How To Remotely Access Raspberry Pi With Remoteiot Download Free A Comprehensive Guide
Table of Contents
- What is AWS IoT SSH Tunnel?
- Key Components of AWS IoT SSH Tunnel
- How AWS IoT SSH Tunnel Works
- Step-by-Step Setup Process
- Security Features and Best Practices
- Common Use Cases and Applications
- Performance Considerations
- Troubleshooting Common Issues
- Comparison with Other Remote Access Solutions
- Conclusion and Next Steps
What is AWS IoT SSH Tunnel?
AWS IoT SSH Tunnel is a specialized service that enables secure remote access to IoT devices through the AWS IoT platform. Unlike traditional SSH connections that require direct IP access, this service leverages AWS IoT's secure communication channels to establish encrypted tunnels between your local machine and remote IoT devices.
The service operates by creating a virtual tunnel through AWS IoT Core, allowing administrators and developers to access their IoT devices securely without exposing them directly to the internet. This approach significantly reduces the attack surface and provides enhanced security for remote management operations.
Key Benefits of Using AWS IoT SSH Tunnel
- Enhanced Security: Utilizes AWS IoT's robust security features and end-to-end encryption.
- Scalability: Supports large-scale IoT deployments with minimal configuration.
- Cost-Effective: Eliminates the need for complex network configurations or additional infrastructure.
- Reliability: Backed by AWS's global infrastructure and high availability guarantees.
Key Components of AWS IoT SSH Tunnel
Understanding the core components of AWS IoT SSH Tunnel is essential for proper implementation and management. These components work together to create a secure and efficient remote access solution.
AWS IoT Core
AWS IoT Core serves as the foundation of the SSH Tunnel service. It provides the necessary infrastructure for device registration, authentication, and secure communication. Key features include:
- Device Registry: Maintains a secure database of registered devices.
- Authentication Mechanisms: Supports X.509 certificates, IAM credentials, and custom authorizers.
- Message Broker: Facilitates secure communication between devices and the AWS cloud.
Tunneling Service
The tunneling service component handles the actual creation and management of SSH tunnels. It includes:
- Tunnel Manager: Responsible for creating, maintaining, and terminating tunnels.
- Endpoint Configuration: Defines access points for tunnel connections.
- Session Management: Tracks active tunnel sessions and their statuses.
Security Layer
The security layer implements multiple protection mechanisms:
Read also:Vnc Connect Iot Free A Comprehensive Guide To Remote Access Solutions
- End-to-End Encryption: Utilizes TLS 1.2 for all communications.
- Access Control: Implements fine-grained permission policies.
- Audit Logging: Maintains detailed records of all tunnel activities.
How AWS IoT SSH Tunnel Works
The AWS IoT SSH Tunnel process involves several key steps that ensure secure and reliable connections:
- Device Registration: IoT devices are registered in AWS IoT Core with unique identities.
- Tunnel Request: Local machine sends a tunnel creation request through AWS IoT Core.
- Authentication: Both local machine and IoT device authenticate through AWS security mechanisms.
- Tunnel Establishment: Secure tunnel is created between local machine and IoT device.
- Data Transmission: SSH traffic is encrypted and transmitted through the tunnel.
- Session Termination: Tunnel is automatically closed after use or based on timeout settings.
Traffic Flow Diagram
1. Local Machine → AWS IoT Core → IoT Device
2. All traffic encrypted using TLS 1.2
3. Authentication verified at each step
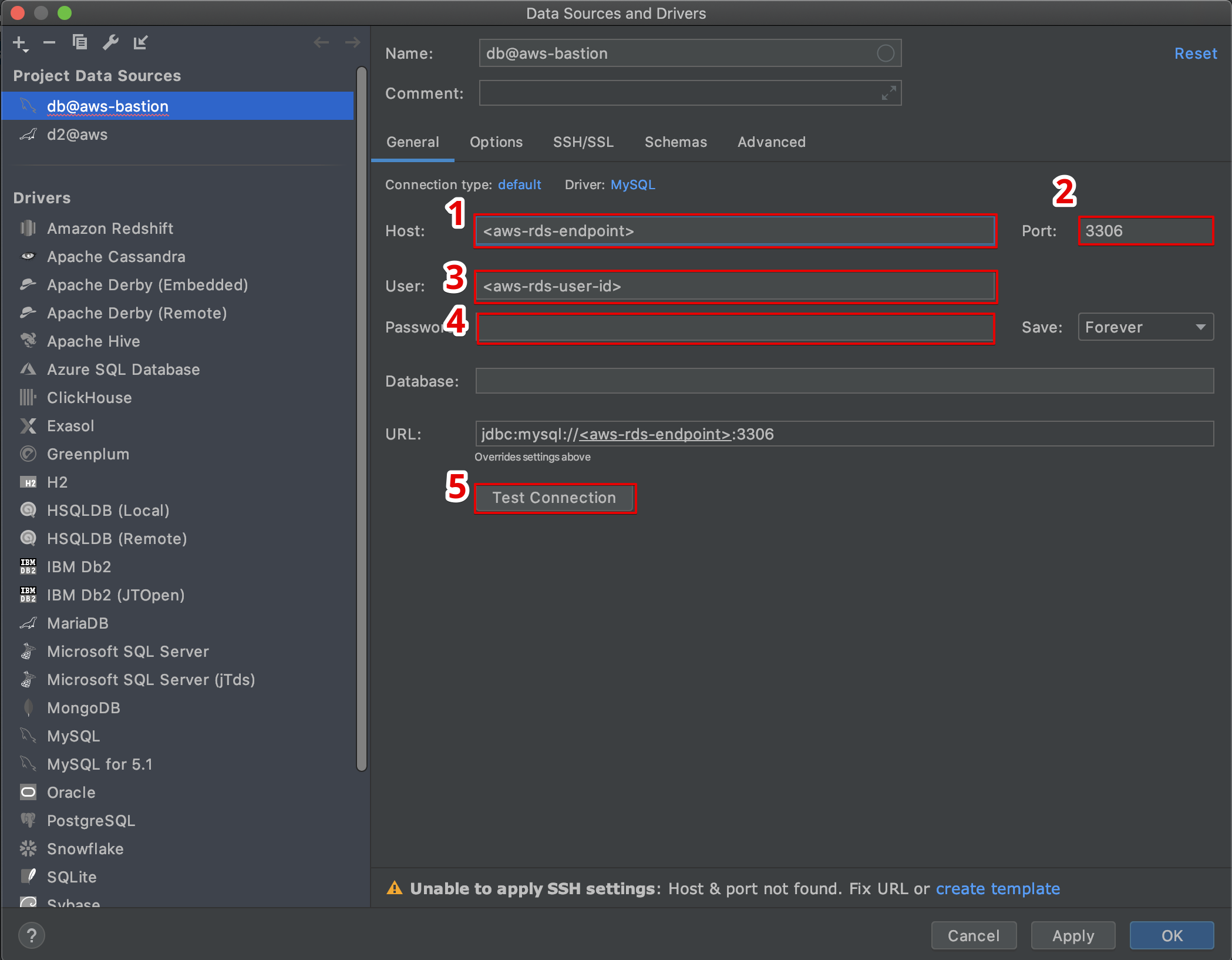
Step-by-Step Setup Process
Implementing AWS IoT SSH Tunnel requires careful planning and execution. Follow these steps for successful deployment:
Prerequisites
- AWS Account with appropriate permissions
- AWS CLI installed and configured
- Registered IoT devices in AWS IoT Core
- SSH client installed on local machine
Step 1: Configure AWS IoT Core
Create and configure your AWS IoT Core environment:
- Set up Thing Registry
- Create and attach security policies
- Generate and register device certificates
Step 2: Enable Tunneling Service
Activate and configure the tunneling service:
- Enable IoT Device Management
- Configure tunnel endpoints
- Set up access control policies
Step 3: Establish SSH Tunnel
Connect to your IoT device:
- Initiate tunnel creation from local machine
- Authenticate using IAM credentials
- Establish SSH connection through tunnel
Security Features and Best Practices
AWS IoT SSH Tunnel incorporates multiple layers of security to protect your remote connections. Understanding these features and implementing best practices is crucial for maintaining a secure environment.
Authentication Mechanisms
- X.509 Certificates: Provides strong device authentication.
- IAM Roles and Policies: Controls access to tunneling resources.
- Custom Authorizers: Allows integration with existing authentication systems.
Encryption Protocols
- TLS 1.2: Secures all communications.
- SSH Encryption: Protects terminal sessions.
- Data Encryption at Rest: Protects stored credentials and configurations.
Recommended Security Practices
- Implement least privilege access policies.
- Regularly rotate security credentials.
- Enable CloudWatch logging for monitoring.
- Use VPC endpoints for private connectivity.
Common Use Cases and Applications
AWS IoT SSH Tunnel serves various practical applications across different industries:
Industrial Automation
- Remote maintenance of manufacturing equipment
- Secure access to SCADA systems
- Real-time monitoring of production lines
Smart Buildings
- Remote management of building automation systems
- Secure access to HVAC controls
- Monitoring of security systems
Healthcare
- Remote maintenance of medical devices
- Secure access to patient monitoring systems
- Compliance with HIPAA regulations
Performance Considerations
Optimizing the performance of AWS IoT SSH Tunnel requires attention to several factors:
Latency Optimization
- Choose nearest AWS region for tunnel endpoints
- Use AWS Global Accelerator for improved connectivity
- Optimize network configurations
Throughput Enhancement
- Enable connection reuse
- Implement compression where appropriate
- Monitor and adjust buffer sizes
Scalability Planning
- Design for horizontal scaling
- Implement automated scaling policies
- Monitor resource utilization regularly
Troubleshooting Common Issues
When working with AWS IoT SSH Tunnel, you may encounter various issues. Here are solutions to common problems:
Connection Failures
- Verify device registration status
- Check security policies and permissions
- Validate network connectivity
Performance Degradation
- Analyze CloudWatch metrics
- Check for resource bottlenecks
- Review tunnel configuration settings
Security Alerts
- Review access logs
- Rotate compromised credentials
- Update security policies
Comparison with Other Remote Access Solutions
Understanding how AWS IoT SSH Tunnel compares to other remote access solutions can help you make informed decisions:
| Feature | AWS IoT SSH Tunnel | Traditional SSH | VPN Solutions |
|---|---|---|---|
| Security | High (End-to-End Encryption) | Medium | High |
| Scalability | Excellent | Poor | Good |
| Cost | Pay-as-you-go | Low | High |
| Setup Complexity | Medium | Low | High |
Conclusion and Next Steps
AWS IoT SSH Tunnel provides a powerful and secure solution for managing remote IoT devices. By leveraging AWS's robust infrastructure and security features, organizations can establish reliable remote connections while maintaining high security standards. Throughout this guide, we've explored the core components, implementation process, security features, and practical applications of this service.
As you consider implementing AWS IoT SSH Tunnel in your organization, remember to:
- Conduct thorough testing in a staging environment
- Implement comprehensive monitoring and logging
- Regularly review and update security policies
- Train your team on proper usage and best practices
Ready to take the next step? We encourage you to explore AWS documentation for detailed technical specifications and implementation guides. Share your experiences or questions in the comments below, and help build a community of IoT professionals working to enhance remote access security.
For more information about AWS IoT services and security best practices, visit the official AWS IoT documentation.