Are you looking for a reliable and free way to manage your IoT devices remotely? VNC SSH IoT Free solutions offer a powerful combination of secure access and ease of use. In today’s interconnected world, managing IoT devices efficiently is crucial for both personal and professional environments. This guide will explore how VNC and SSH can work together to provide secure and seamless remote access to your IoT devices.
With the increasing number of IoT devices being deployed across industries, the need for secure remote management has become more important than ever. Many users are unaware of the potential risks associated with unsecured remote access methods. This article will provide you with comprehensive information about using VNC and SSH for IoT device management, including step-by-step guidance, security considerations, and practical implementation tips.
Whether you're a developer, system administrator, or IoT enthusiast, understanding how to implement secure remote access is essential. We'll explore various free solutions available in the market, discuss their features, and provide expert recommendations to help you make informed decisions about managing your IoT infrastructure securely.
Read also:Vnc Connect Iot Free A Comprehensive Guide To Remote Access Solutions
Table of Contents
- Understanding VNC SSH IoT
- Benefits of Using VNC SSH for IoT Management
- Key Features of Free VNC SSH Solutions
- Security Considerations for Remote IoT Access
- Step-by-Step Setup Guide
- Popular Free VNC SSH IoT Solutions
- Performance Optimization Techniques
- Troubleshooting Common Issues
- Future Trends in IoT Remote Management
- Conclusion and Recommendations
Understanding VNC SSH IoT
VNC (Virtual Network Computing) and SSH (Secure Shell) represent two fundamental technologies that, when combined, create a powerful solution for IoT device management. VNC enables graphical remote desktop access, allowing users to interact with IoT devices as if they were physically present. SSH, on the other hand, provides a secure encrypted tunnel for command-line access and data transfer.
The integration of these technologies offers several distinct advantages:
- End-to-end encryption for all remote sessions
- Secure authentication mechanisms
- Ability to manage multiple devices from a single interface
- Platform-independent access across different operating systems
When implementing VNC SSH IoT solutions, it's crucial to understand the underlying architecture. The SSH protocol creates a secure connection between the client and server, while VNC operates within this encrypted tunnel. This combination ensures that all remote interactions with IoT devices are protected from unauthorized access and potential security threats.
Benefits of Using VNC SSH for IoT Management
The combination of VNC and SSH offers numerous advantages for IoT device management:
Enhanced Security Features
Security remains the top priority when managing IoT devices remotely. The VNC SSH combination provides:
- 256-bit AES encryption for all data transmissions
- Two-factor authentication support
- IP whitelisting capabilities
- Session logging and monitoring
Improved Accessibility
Free VNC SSH solutions enable users to:
Read also:Did Barron Trump Release A Song Exploring The Rumors And Facts
- Access devices from any location with internet connectivity
- Use multiple devices (PC, tablet, smartphone) for remote management
- Implement cross-platform compatibility
- Support both GUI and CLI interfaces
These benefits make VNC SSH particularly valuable for managing distributed IoT networks across different geographical locations.
Key Features of Free VNC SSH Solutions
When evaluating free VNC SSH solutions for IoT management, consider these essential features:
Core Functionalities
- Real-time remote desktop access with low latency
- File transfer capabilities through secure channels
- Multiple concurrent connection support
- Customizable security settings
Advanced Capabilities
- Automated session recording
- Resource monitoring tools
- Device grouping and organization
- Alert notifications for security events
Many free solutions offer comparable features to their paid counterparts, making them excellent choices for small to medium-sized IoT deployments.
Security Considerations for Remote IoT Access
Securing remote access to IoT devices requires careful planning and implementation:
Best Practices for Secure Connections
- Use strong, unique passwords for all accounts
- Implement SSH key-based authentication
- Regularly update software and firmware
- Enable firewall protection and port restrictions
Common Security Threats
- Brute force attacks on SSH ports
- Man-in-the-middle attacks
- Unauthorized access attempts
- Data interception during transmission
By following these security guidelines, you can significantly reduce the risk of compromising your IoT infrastructure.
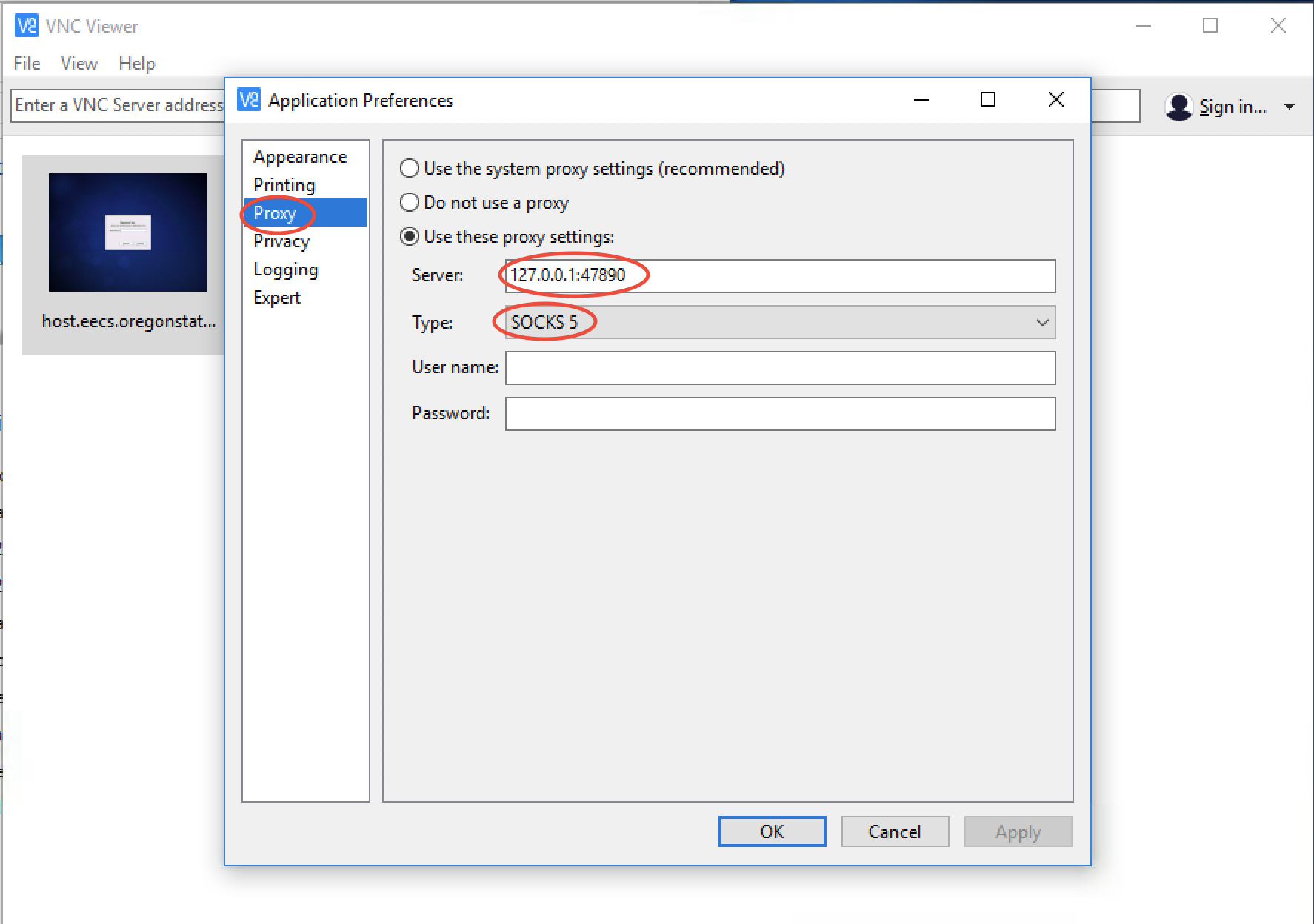
Step-by-Step Setup Guide
Implementing VNC SSH for IoT devices involves several key steps:
Initial Configuration
- Install SSH server on the IoT device
- Configure SSH settings (port, authentication methods)
- Set up firewall rules to restrict access
- Install VNC server software
Client-Side Setup
- Download and install VNC client software
- Configure SSH tunnel settings
- Test connection using basic commands
- Verify GUI access through VNC
Each step requires careful attention to detail to ensure proper functionality and security.
Popular Free VNC SSH IoT Solutions
Several free solutions stand out in the VNC SSH IoT space:
Top Recommendations
- TightVNC with OpenSSH integration
- RealVNC Community Edition
- TigerVNC with SSH tunneling support
- UltraVNC with secure extensions
Each solution offers unique features and capabilities, making it essential to evaluate them based on your specific requirements.
Performance Optimization Techniques
Optimizing VNC SSH performance involves several strategies:
Network Optimization
- Enable compression for SSH connections
- Adjust VNC color depth settings
- Use persistent connections
- Implement bandwidth throttling
Device-Specific Tuning
- Optimize device resources allocation
- Adjust screen resolution settings
- Implement caching mechanisms
- Use hardware acceleration when available
These optimization techniques can significantly improve remote access performance, especially for resource-constrained IoT devices.
Troubleshooting Common Issues
When working with VNC SSH IoT solutions, you may encounter various challenges:
Connection Problems
- Verify network connectivity and firewall settings
- Check SSH port configuration
- Review authentication credentials
- Examine log files for error messages
Performance Issues
- Adjust VNC quality settings
- Optimize SSH compression levels
- Reduce desktop resolution
- Limit concurrent connections
Having a systematic approach to troubleshooting can help quickly resolve most common problems.
Future Trends in IoT Remote Management
The field of IoT remote management continues to evolve with several emerging trends:
Technological Advancements
- Integration with AI-based monitoring systems
- Enhanced security protocols
- Cloud-based management platforms
- Improved user interface designs
Industry Developments
- Increased adoption in industrial IoT applications
- Development of specialized IoT management tools
- Expansion of 5G-enabled remote access solutions
- Implementation of blockchain security features
These trends indicate a promising future for secure and efficient IoT device management.
Conclusion and Recommendations
In conclusion, VNC SSH IoT Free solutions provide a robust framework for managing IoT devices remotely. The combination of secure SSH connections with VNC's graphical capabilities offers users a powerful toolset for efficient device management. Throughout this guide, we've explored the technical aspects, security considerations, and practical implementation steps necessary for successful deployment.
We recommend starting with a thorough evaluation of your specific IoT management needs. Consider factors such as the number of devices, required access frequency, and security requirements when selecting a solution. For most users, a combination of TightVNC and OpenSSH provides an excellent balance of features and security.
We encourage you to share your experiences with VNC SSH IoT solutions in the comments below. If you found this guide helpful, please consider sharing it with your network. For more information on IoT management and security, explore our other articles covering related topics and advanced implementation strategies.