In today's interconnected world, the ability to remotely manage IoT devices has become essential for businesses and individuals alike. One of the most effective ways to achieve this is through the use of remote SSH on an IoT platform designed for Android devices. Secure Shell (SSH) provides a secure method for accessing and controlling devices over a network, ensuring that sensitive data remains protected while enabling seamless management. With the growing adoption of IoT technologies, leveraging remote SSH on Android platforms has emerged as a critical solution for enhancing operational efficiency and maintaining robust cybersecurity.
As the Internet of Things continues to expand, the demand for reliable remote access solutions has increased dramatically. Android-based IoT platforms offer unique advantages due to their widespread adoption, flexibility, and powerful capabilities. These platforms enable users to establish secure connections with their IoT devices from anywhere in the world, facilitating real-time monitoring, configuration updates, and troubleshooting. The combination of SSH protocol security and Android's versatile ecosystem creates an ideal environment for managing complex IoT networks while maintaining stringent security standards.
This comprehensive guide will explore the various aspects of remote SSH implementation on Android-based IoT platforms. From understanding the fundamental principles to practical implementation strategies, we'll cover everything you need to know to establish and maintain secure remote connections. Whether you're a system administrator, IoT developer, or technology enthusiast, this article will provide valuable insights into optimizing your IoT management capabilities while ensuring maximum security and efficiency.
Read also:Iot Platform Remote Ssh Download A Comprehensive Guide For Secure Device Management
Table of Contents
- Understanding Remote SSH in IoT Ecosystems
- Android-Based IoT Platforms: Features and Benefits
- Implementing Secure Remote SSH Connections
- Security Best Practices for Remote SSH Access
- Advanced Features and Capabilities
- Troubleshooting Common Issues
- Performance Optimization Techniques
- Future Trends in IoT Remote Management
- Case Studies: Successful Implementations
- Conclusion and Next Steps
Understanding Remote SSH in IoT Ecosystems
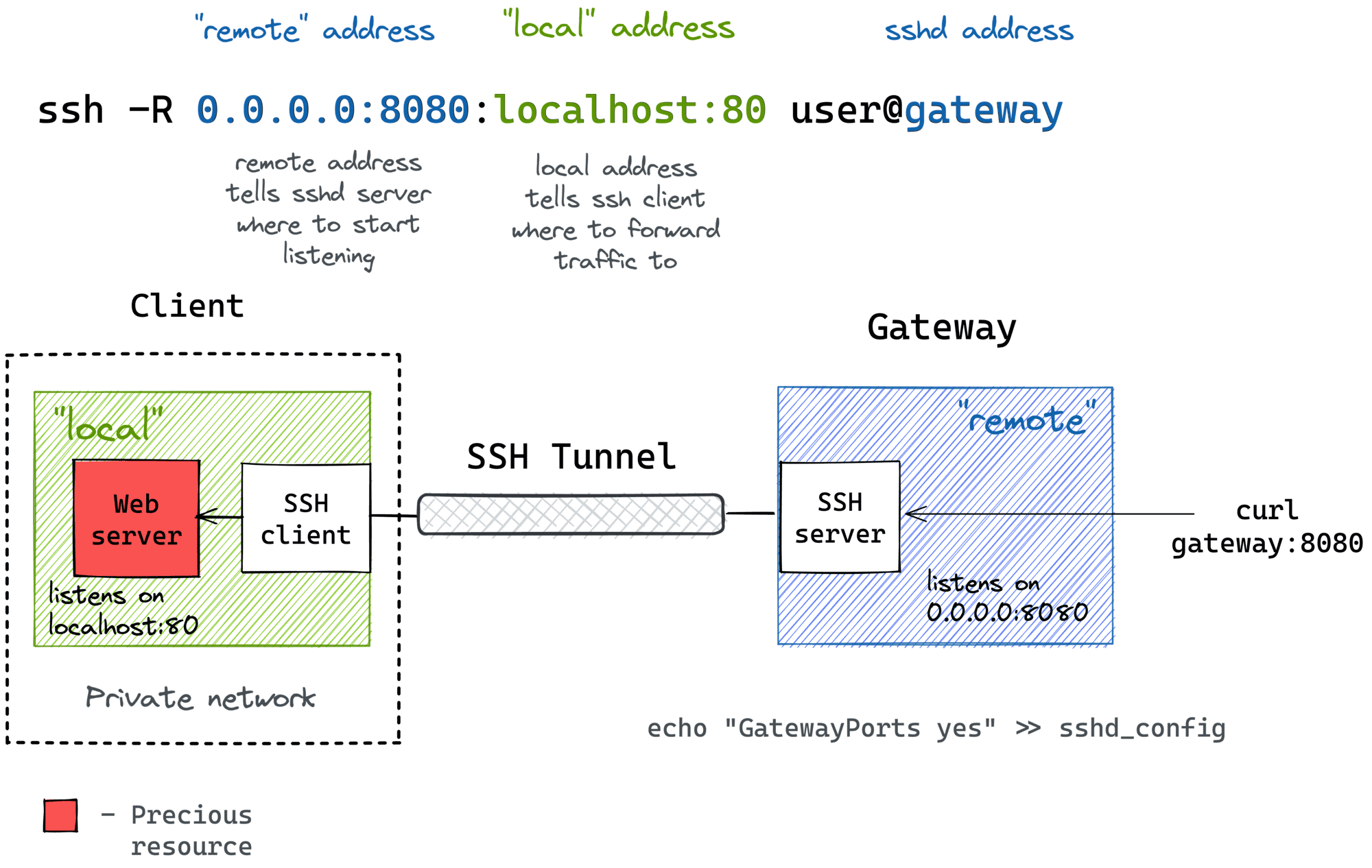
Remote SSH serves as a fundamental protocol for secure communication in IoT environments. At its core, SSH establishes encrypted connections between devices, enabling administrators to execute commands, transfer files, and manage system configurations remotely. This protocol utilizes strong encryption algorithms and authentication mechanisms to ensure data integrity and confidentiality. In IoT ecosystems, where numerous devices often operate across different networks, remote SSH provides a standardized method for secure access and management.
Key Components of Remote SSH Architecture
The architecture of remote SSH in IoT platforms typically consists of several critical components:
- SSH Server: Installed on target IoT devices, handling incoming connection requests
- SSH Client: Installed on administrator devices, initiating connection attempts
- Authentication Mechanisms: Including password-based, key-based, and certificate-based methods
- Encryption Protocols: Utilizing AES, RSA, and other secure algorithms for data protection
- Port Forwarding: Enabling secure tunneling of network traffic between devices
Benefits of Remote SSH in IoT Management
Implementing remote SSH in IoT platforms offers numerous advantages:
- Enhanced Security: Protects against unauthorized access through robust encryption
- Remote Accessibility: Enables management from anywhere with internet connectivity
- Automation Capabilities: Supports script execution for routine maintenance tasks
- Real-time Monitoring: Facilitates immediate response to system alerts and issues
- Platform Independence: Works across different operating systems and device types
Android-Based IoT Platforms: Features and Benefits
Android-based IoT platforms have gained significant traction due to their versatility and widespread adoption. These platforms leverage Android's robust architecture to create powerful IoT management solutions that integrate seamlessly with existing enterprise systems. The Android operating system's flexibility allows developers to create custom applications specifically designed for IoT device management, while maintaining compatibility with standard Android devices.
Technical Specifications of Android IoT Platforms
| Feature | Description |
|---|---|
| Operating System | Android 10 or higher (IoT optimized) |
| Processor Support | ARM, x86, and MIPS architectures |
| Memory Requirements | Minimum 1GB RAM, Recommended 2GB+ |
| Storage Capacity | 8GB minimum, expandable via microSD |
| Connectivity Options | Wi-Fi, Bluetooth, Ethernet, Cellular |
| Security Features | Hardware-backed keystore, SELinux, Verified Boot |
Advantages of Android-Based Solutions
The adoption of Android-based IoT platforms offers several distinct advantages:
- Developer Ecosystem: Access to extensive Android development tools and resources
- App Compatibility: Ability to run standard Android applications alongside IoT-specific software
- Scalability: Supports deployment across small-scale to enterprise-level implementations
- Regular Updates: Continuous security patches and feature enhancements from Google
- Cost-Effectiveness: Utilizes existing Android hardware and development expertise
Implementing Secure Remote SSH Connections
Setting up remote SSH on Android-based IoT platforms requires careful planning and execution. The implementation process typically involves several key steps, starting from initial configuration to establishing secure connections. Proper setup ensures both functionality and security, minimizing potential vulnerabilities while maximizing operational efficiency.
Read also:How To Use Ssh On Iot Devices Anywhere With Android
Step-by-Step Implementation Guide
- System Preparation: Ensure all devices meet minimum requirements and have necessary permissions enabled
- SSH Server Installation: Deploy SSH server software on target IoT devices
- Configuration Setup: Customize SSH settings for optimal security and performance
- Authentication Setup: Implement multi-factor authentication mechanisms
- Network Configuration: Configure firewall rules and port forwarding settings
- Testing and Validation: Verify connection stability and security measures
Configuration Parameters and Best Practices
When configuring remote SSH connections, consider the following parameters:
- Use non-standard SSH ports to reduce automated attack risks
- Implement IP whitelisting for additional access control
- Enable logging and monitoring for connection attempts
- Regularly update SSH server software and dependencies
- Limit root access and use privilege separation techniques
Security Best Practices for Remote SSH Access
Maintaining robust security measures is crucial when implementing remote SSH on IoT platforms. As these systems often handle sensitive data and control critical infrastructure, following established security protocols becomes essential. The following best practices help ensure the integrity and confidentiality of remote connections while protecting against potential threats.
Authentication and Access Control
Implementing strong authentication mechanisms forms the foundation of secure remote SSH access:
- Use SSH key pairs instead of password-based authentication
- Implement multi-factor authentication (MFA) where possible
- Regularly rotate SSH keys and update access credentials
- Implement role-based access control (RBAC) for user management
- Maintain an up-to-date inventory of authorized devices and users
Network Security Measures
To protect remote SSH connections from network-based threats:
- Use secure protocols for all data transmissions
- Implement network segmentation to isolate IoT devices
- Regularly scan for and patch known vulnerabilities
- Monitor network traffic for unusual patterns or anomalies
- Use intrusion detection and prevention systems (IDPS)
Advanced Features and Capabilities
Modern remote SSH implementations on Android-based IoT platforms offer several advanced features that enhance functionality and security. These capabilities extend beyond basic remote access, providing powerful tools for system administration and management.
Automation and Scripting Capabilities
Remote SSH enables sophisticated automation through various scripting options:
- Automated backup and restore procedures
- Scheduled maintenance tasks and system updates
- Custom monitoring scripts with alert notifications
- Automated configuration management across devices
- Centralized logging and reporting mechanisms
Integration with Other Services
Modern SSH implementations support seamless integration with various services:
- Cloud storage and backup solutions
- Monitoring and analytics platforms
- Security information and event management (SIEM) systems
- Device management and provisioning tools
- Third-party authentication services
Troubleshooting Common Issues
Despite careful implementation, remote SSH connections may encounter various issues. Understanding common problems and their solutions helps maintain system reliability and minimizes downtime. The following troubleshooting guide addresses frequent challenges faced by administrators managing Android-based IoT platforms.
Connection Problems and Solutions
Common connection issues include:
- Timeout errors: Verify network connectivity and firewall settings
- Authentication failures: Check SSH key configurations and permissions
- Slow connections: Optimize SSH configuration parameters and network settings
- Intermittent disconnections: Implement keep-alive settings and monitor network stability
- Port conflicts: Use non-standard ports and verify port forwarding rules
Performance Optimization Techniques
To enhance SSH performance:
- Use compression for data transfer when appropriate
- Optimize cipher and MAC algorithms selection
- Implement connection pooling for multiple sessions
- Use persistent connections for frequent access
- Regularly monitor and adjust buffer sizes
Performance Optimization Techniques
Optimizing remote SSH performance on Android-based IoT platforms requires attention to various technical aspects. These optimization strategies help maintain efficient connections while minimizing resource consumption on both client and server devices.
Server-Side Optimization
On the server side, implement the following optimizations:
- Use efficient encryption algorithms to reduce processing overhead
- Implement connection multiplexing to handle multiple sessions
- Optimize keep-alive settings to maintain stable connections
- Regularly clean up inactive sessions and resources
- Monitor server load and adjust configuration parameters accordingly
Client-Side Optimization
For client devices, consider these optimization techniques:
- Use lightweight SSH clients optimized for mobile devices
- Implement local caching for frequently accessed data
- Optimize network settings for mobile connections
- Use background services for maintaining persistent connections
- Implement power-saving features to extend battery life
Future Trends in IoT Remote Management
The landscape of remote SSH and IoT management continues to evolve rapidly, driven by technological advancements and changing security requirements. Several emerging trends are shaping the future of remote device management on Android-based platforms.
Emerging Technologies and Innovations
Key developments in remote IoT management include:
- Integration with artificial intelligence for predictive maintenance
- Adoption of quantum-resistant encryption algorithms
- Implementation of blockchain technology for secure transactions
- Development of edge computing capabilities for local processing
- Enhanced mobile device management (MDM) features
Industry Standards and Regulations
Upcoming standards and regulations will impact remote management practices: