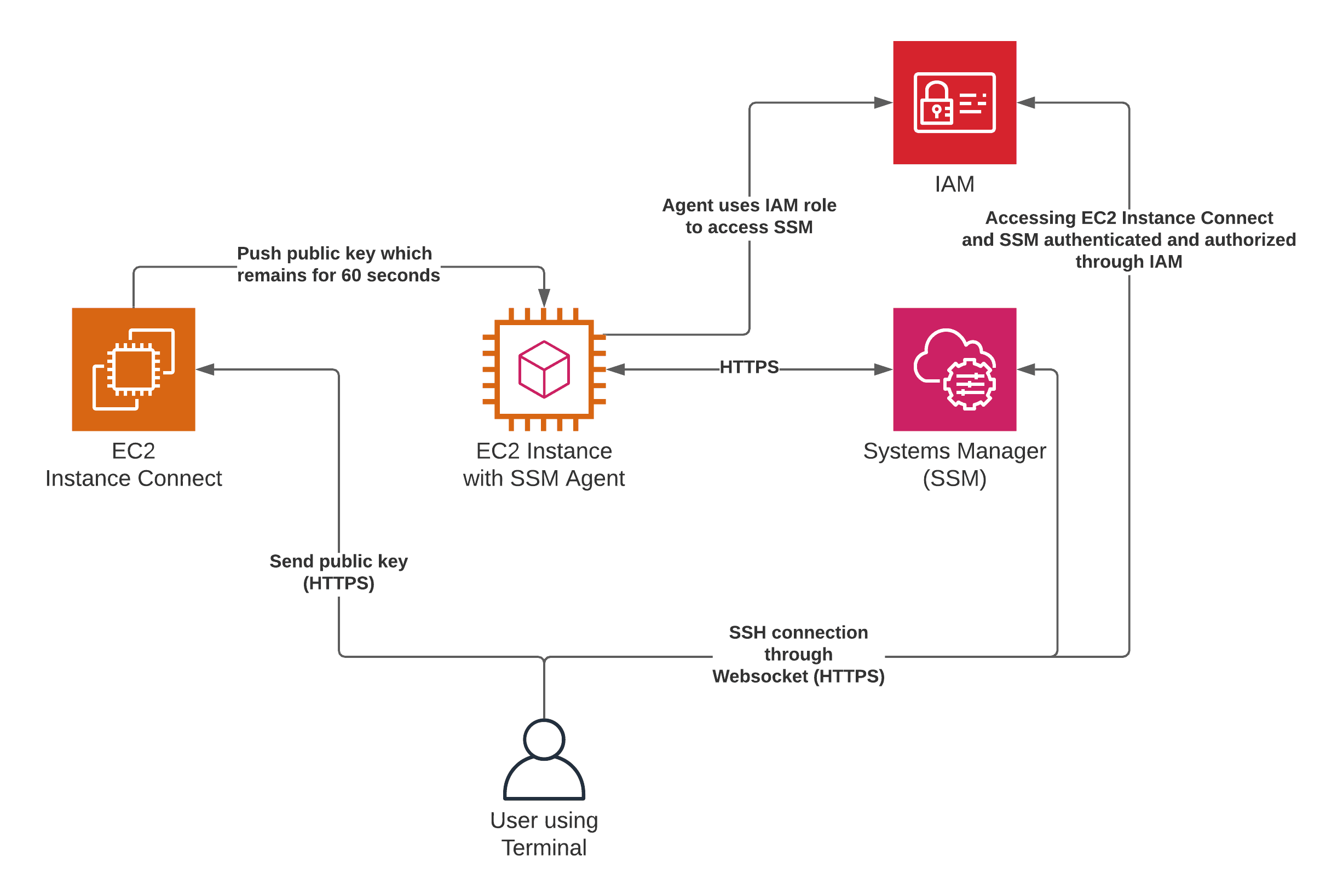
Connecting to an IoT device over the internet using SSH can be a game-changer for remote management and troubleshooting. Whether you're a developer, IT professional, or tech enthusiast, mastering this process can help you maintain your IoT infrastructure seamlessly. However, many users face challenges when trying to establish an SSH connection without port forwarding. This article will guide you step-by-step on how to connect SSH IoT devices over the internet on a Mac without relying on port forwarding.
Secure Shell (SSH) is a protocol that allows secure communication between two devices. IoT devices, which are increasingly being used in homes and businesses, often require remote access for maintenance and monitoring. While SSH is a powerful tool, traditional methods like port forwarding can be complex and expose your network to security risks. This guide focuses on alternative methods to connect SSH IoT devices securely without port forwarding, ensuring a smooth and secure experience.
By the end of this article, you will have a clear understanding of how to establish an SSH connection to your IoT device from anywhere in the world using your Mac. We'll explore tools and techniques that are beginner-friendly yet robust enough for advanced users. Let's dive into the details and unlock the potential of remote IoT management.
Read also:Tim Tebow Contract A Journey Through The Nfl And Beyond
Table of Contents
- Introduction to SSH and IoT Devices
- Challenges of Connecting IoT Devices Without Port Forwarding
- Tools You Can Use to Connect SSH IoT Devices
- Using Ngrok for Secure SSH Connections
- ZeroTier: A Virtual Network Solution
- Tailscale: Simplifying Secure Connections
- Understanding SSH Tunneling Without Port Forwarding
- Best Practices for Secure SSH Connections
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to SSH and IoT Devices
SSH, or Secure Shell, is a cryptographic network protocol used for secure data communication, remote command execution, and other secure network services between two devices. It is widely used in IoT (Internet of Things) environments to manage and configure devices remotely. IoT devices, such as smart home gadgets, industrial sensors, and embedded systems, often require remote access for updates, diagnostics, and maintenance.
When connecting IoT devices over the internet, SSH provides an encrypted channel to ensure data integrity and confidentiality. However, traditional methods like port forwarding can be cumbersome and may expose your network to potential threats. Port forwarding involves configuring your router to direct incoming traffic to a specific device, which can be complex and risky if not done correctly.
This is where alternative methods come into play. By leveraging tools and techniques that bypass the need for port forwarding, you can securely connect to your IoT devices from anywhere in the world. These methods not only simplify the process but also enhance security by reducing the attack surface of your network.
Challenges of Connecting IoT Devices Without Port Forwarding
Connecting IoT devices over the internet without port forwarding presents several challenges. Understanding these challenges is crucial to finding effective solutions. Below are some of the most common issues:
- Firewall Restrictions: Many routers and ISPs block incoming connections by default, making it difficult to establish a direct SSH connection.
- Dynamic IP Addresses: IoT devices often use dynamic IP addresses, which can change frequently and make it hard to maintain a stable connection.
- Security Risks: Exposing your network to the internet increases the risk of unauthorized access and cyberattacks.
- Complexity: Configuring traditional methods like port forwarding can be technically challenging for non-experts.
To overcome these challenges, alternative tools and techniques have been developed. These solutions focus on creating secure, encrypted tunnels that bypass the need for port forwarding while maintaining a high level of security.
Tools You Can Use to Connect SSH IoT Devices
Several tools can help you connect to your IoT devices over the internet without port forwarding. Each tool has its own strengths and is suitable for different use cases. Below are some of the most popular options:
Read also:Breeding Visa Japan A Comprehensive Guide For Aspiring Breeders
Ngrok
Ngrok is a powerful tool that creates secure tunnels to your localhost, allowing you to expose your IoT device to the internet without port forwarding. It works by providing a public URL that routes traffic to your local device securely.
ZeroTier
ZeroTier creates a virtual private network (VPN) that connects your devices as if they were on the same local network. This eliminates the need for port forwarding and simplifies remote access to IoT devices.
Tailscale
Tailscale is a modern VPN solution that leverages the WireGuard protocol for secure and fast connections. It is easy to set up and provides a seamless experience for connecting IoT devices remotely.
Using Ngrok for Secure SSH Connections
Ngrok is an excellent choice for establishing SSH connections to IoT devices without port forwarding. Here's how you can use it:
- Download and Install Ngrok: Visit the official Ngrok website and download the tool. Install it on your Mac by following the instructions provided.
- Set Up an Account: Create an account on Ngrok to access advanced features and generate an authentication token.
- Start Ngrok Tunnel: Use the command line to start a tunnel to your IoT device. For example, run
ngrok tcp 22to expose port 22 (SSH) to the internet. - Connect via SSH: Use the public URL provided by Ngrok to connect to your IoT device. For example, run
ssh username@tcp.ngrok.io:port.
Ngrok is a reliable and user-friendly tool that simplifies the process of connecting IoT devices over the internet. However, it is important to note that free accounts have limitations, such as session timeouts and limited bandwidth.
ZeroTier: A Virtual Network Solution
ZeroTier is another powerful tool for connecting IoT devices without port forwarding. It creates a virtual network that connects your devices securely, regardless of their physical location. Here's how to set it up:
- Sign Up and Install ZeroTier: Create an account on the ZeroTier website and download the application for your Mac and IoT device.
- Create a Network: Log in to the ZeroTier Central dashboard and create a new network. Note the network ID.
- Join the Network: Install ZeroTier on your IoT device and join the network using the network ID.
- Assign IP Addresses: Configure static IP addresses for your devices within the ZeroTier network.
- Connect via SSH: Use the assigned IP address to connect to your IoT device via SSH.
ZeroTier is ideal for users who need a permanent and secure connection to their IoT devices. It eliminates the need for port forwarding and provides a seamless experience for remote management.
Tailscale: Simplifying Secure Connections
Tailscale is a modern VPN solution that simplifies secure connections between devices. It uses the WireGuard protocol for fast and secure communication. Here's how to use Tailscale for SSH connections:
- Download and Install Tailscale: Install Tailscale on your Mac and IoT device by following the instructions on the official website.
- Sign In: Use your Google or Microsoft account to sign in to Tailscale.
- Connect Devices: Once signed in, your devices will automatically appear in the Tailscale dashboard.
- Connect via SSH: Use the Tailscale-assigned IP address to connect to your IoT device via SSH.
Tailscale is an excellent choice for users who prioritize simplicity and security. It requires minimal configuration and provides a reliable connection for remote IoT management.
Understanding SSH Tunneling Without Port Forwarding
SSH tunneling is a technique that allows you to forward traffic securely between two devices without exposing your network to the internet. This method can be used to connect to IoT devices without port forwarding. Here's how it works:
- Set Up a Reverse SSH Tunnel: Use the
ssh -Rcommand to create a reverse tunnel from your IoT device to a remote server. - Access the Remote Server: Connect to the remote server using SSH and access your IoT device through the tunnel.
SSH tunneling is a powerful method for secure remote access, but it requires a remote server to act as an intermediary. This approach is ideal for advanced users who have access to a remote server.
Best Practices for Secure SSH Connections
When connecting IoT devices over the internet, security should be a top priority. Here are some best practices to ensure secure SSH connections:
- Use Strong Passwords: Avoid using default passwords and choose strong, unique passwords for your IoT devices.
- Enable Key-Based Authentication: Use SSH keys instead of passwords for authentication to enhance security.
- Disable Root Login: Prevent unauthorized access by disabling root login and using a regular user account.
- Update Firmware Regularly: Keep your IoT device's firmware up to date to patch vulnerabilities.
By following these best practices, you can minimize the risk of unauthorized access and ensure a secure connection to your IoT devices.
Troubleshooting Common Issues
While connecting IoT devices over the internet, you may encounter some common issues. Below are troubleshooting tips for resolving these problems:
- Connection Refused: Ensure that the SSH service is running on your IoT device and that the correct port is being used.
- Timeout Errors: Check your firewall settings and ensure that the tool you're using is properly configured.
- Authentication Failures: Verify that your SSH keys or passwords are correct and that key-based authentication is enabled.
If you continue to experience issues, consult the documentation for the tool you're using or seek assistance from online communities and forums.
Conclusion and Next Steps
In this article, we explored how to connect SSH IoT devices over the internet on a Mac without relying on port forwarding. By leveraging tools like Ngrok, ZeroTier, and Tailscale, you can establish secure and reliable connections to your IoT devices from anywhere in the world. We also discussed best practices for securing SSH connections and troubleshooting common issues.
Now that you have a comprehensive understanding of the process, it's time to put your knowledge into practice. Start by choosing the tool that best suits your needs and follow the step-by-step instructions provided in this guide. If you have any questions or need further assistance, feel free to leave a comment below or share this article with others who might find it helpful. Happy remote managing!